Podcast: Larry Magid speaks with National Cyber Security Alliance (NCSA) Executive Director Michael Kaiser about Wanna Cry and other security threats and precautions
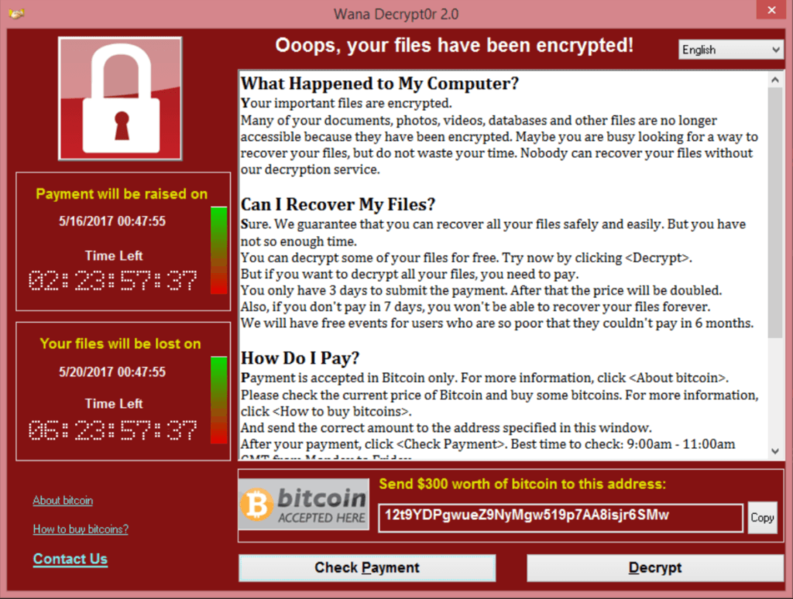
The WanaCry ransomware was aptly named because anyone impacted would “wanna cry.” The attack, which locked hundreds of thousands of users out of their computers by encrypting files, seems to have subsided. The other good news is that relatively few people apparently paid the $300 ransom. Reportedly, as little as $55,000 was paid, which would account for fewer than 200 people.
A piece of bad news – if it’s true – is the theory that North Korea might have been behind the attack. As of this writing, it’s not been confirmed but researchers from Kaspersky Lab, Symantec and Google have found similarities in the WannaCry code and the code used in the North Korean attack against Sony Pictures from 2015.
Several lessons can be learned from this attack. If the North Korea connection is true, both the private sector and government security experts need to shore up defenses against nation-state hacking. Even if North Korea isn’t responsible, it’s a wake-up call.
One way to protect yourself is to have the latest version of the operating system and make sure you have auto-update turned on so that you’ll get all security updates automatically.
Another lesson is that it’s not smart to pay the ransom. Not only does it encourage others to carry out similar crimes, it doesn’t necessarily even work. At a press briefing, the White House’s homeland security adviser said that, as far as he knew, no one who had paid the ransom had their files restored.
It’s also a reminder that we all have a responsibility to protect our own devices. I say this not only because it’s smart to protect yourself, but because it’s beneficial to others if everyone is protected. Just like humans with infectious diseases, infected devices can spread their “viruses” to other devices. Even if you don’t care if your machine is infected, take precautions so that your machine doesn’t wind up turning into a “zombie” that sends spam and malware to others.
So, what follows is some basic device hygiene. I say “device,” because it applies not just to Microsoft Windows but to Macs, Android phones, iPhones and even connected devices like baby cameras, door locks and cars. Any device that uses code (just about everything with a plug or battery these days) can be infected with malicious software and any connected device can spread that software to others.
One way to protect yourself is to have the latest version of the operating system and make sure you have auto-update turned on so that you’ll get all security updates automatically. That’s because once a threat is identified, companies that make operating system and application software often apply “patches” or fixes. Attackers know that not everyone applies those patches, so there are always people who are vulnerable.
In this case, Microsoft had already applied a “patch” or fix for supported versions of Windows but, to take advantage of that fix, users had to have automatic updates turned on or manually update their PCs and they had to have a version of Windows that Microsoft still supports.
Many of those affected by WannaCry were using Windows XP, which Microsoft stopped supporting two years ago. Still, because of the impact of these attacks, Microsoft took the extraordinary step of issuing new fixes, even for XP and other older versions.
You should also be using anti-malware software such as the free Windows Defender that comes with new versions of Windows or commercial products like those from Trend Micro, Symantec and other companies. Some internet service providers offer free versions of commercial software. Comcast, for example, offers Norton security software free to its customers.
Attacks often arrive via email either as attached files or links to websites that have malware or seek personal information that can be used to compromise you or steal your data or money. Don’t open files attached to email, unless you’re expecting it and know it’s safe. And be careful about clicking on any links that come via email, even if they appear to come from your bank or other trusted source. It’s safer to type in the URL directly so you’re sure you’re going to the right site.
It’s also important to have strong and unique passwords or other forms of authentication and to turn on multi-factor authentication that requires you to verify your identify (often from a code sent to your cell phone) before anyone can access your accounts from a device that you haven’t previously used.
Having a backup of all your data files won’t protect you against being infected by malware, but it will greatly limit the damage from any attack that deletes or encrypts your data. I recommend cloud services like Dropbox, Microsoft OneDrive or Carbonite that automatically back up your files in real time on remote servers.
Another option is an external hard drive but, once you backup your files, unplug It from your PC so that if an attack encrypts your files, it won’t encrypt those on the backup disc. But I still prefer cloud services because they not only protect your data from ransomware but also if your computer were destroyed, stolen or broken. Any disaster that destroys your computer might also destroy any backups stored in the same building.
So, if — like most people — you weren’t affected by WannaCry, consider it a wake up call. This won’t be the last massive cyber attack and, while there is no way to guarantee that you’ll be safe, there are some pretty easy ways to minimize the risk to yourself and others.